People spend a lot of money on the Internet. From an individual standpoint, the amount the average person spends on Internet-based services is their largest expense outside of the money they spend on their residence, and perhaps their transportation costs. In order to understand the landscape of what is effectively a battle for Internet supremacy, you first have to take a look at the battlefield itself.
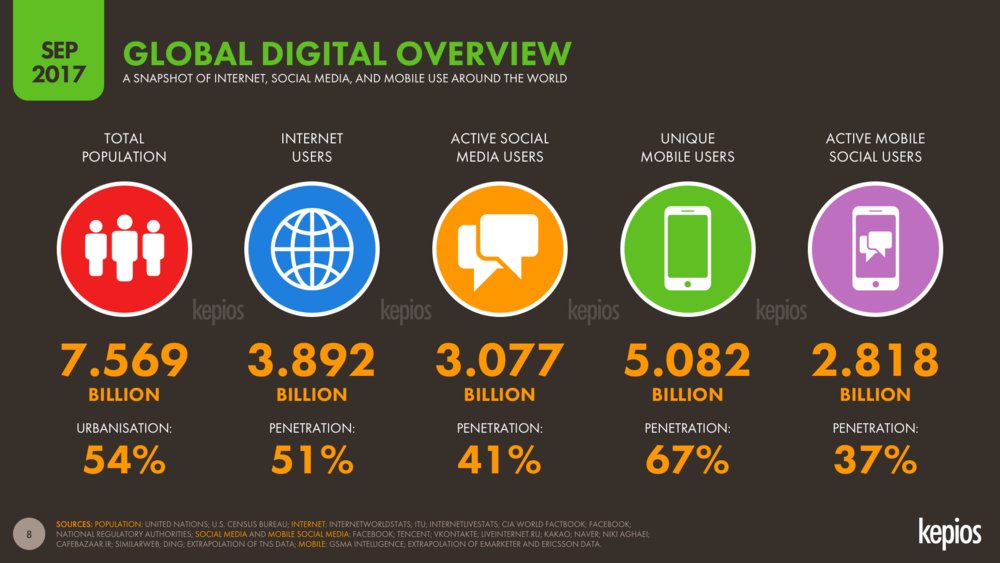
As of September, of the 7.5 billion people on the planet, nearly 3.9 billion of them (51.7%) use the Internet. In North America, 88.1 percent of people (or roughly 320 million) use the Internet in some fashion. This presents opportunities for thousands of companies. Some provide Internet access to would-be consumers. Some deliver content services. Some deliver applications, computing storage, or processing. This has led to the marketing boom you see on the Internet today; and, is where you find a battle raging between the demand created by billions of consumers, and the companies that deliver the services needed to access that customer base.
A lot of questions have been asked recently about what the Internet is. Questions like:
- How do you monetize access to billions of potential customers?
- Should Internet access be free?
- Is Internet access a utility (and thus governed by different rules)?
- Who is in charge of the Internet?
- What is the Internet of Things?
Questions like these produce a variety of answers. With the smoldering embers of the U.S. net neutrality laws suggesting further corporate control of the Internet, we’ll look at the way the Internet is set up in 2018, the costs for businesses and individuals, and why the companies that control access to the Internet are licking their proverbial chops; and, how it challenges the core interpretation of what exactly the Internet is.
The Internet in 2018
The Internet has come a long way in a short time--so far it seems, that it’s hardly recognizable. The Internet of 2018 will continue to be the predominant marketplace in the world. It is seemingly in the process of being consolidated. In fact, 50% of Internet traffic in North America is from 35 websites. In 2007, that same amount of traffic was spread around several thousand websites.
Whether or not a handful of companies own most of it is irrelevant to a consumer, but it’s getting to the point where the product is so consolidated that prices will almost assuredly increase. It’s like Gap Inc. They own The Gap (obviously), Old Navy, Banana Republic, J Crew, H & M, and a few other companies that do largely the same thing: manufacture and sell clothes. Each of these retailers has its own branding and its own management teams, but the money goes to the same place.
The Internet, for all its vastness and entrepreneurial promise, is seemingly controlled, like many industries in the United States, by heavy hitters--companies like Google, Amazon, Facebook, etc. Without playing by their rules, many companies may as well peddle their wares from a kiosk at the local mall. 80% of referral traffic comes from Facebook and Google. This is why many retailers’ sustainability is tied to how they are able to properly advertise their product...for these two company’s search algorithms. Today, tens of thousands of marketing companies have supplied the immense demand to build constructs that meet the demands outlined by the masters of the Internet.
The Cost
The Internet is extremely important to us. Our business, and our clients’ businesses, rely on it every single day. We aren’t alone, and in many ways, the Internet is the newest (and arguably last) frontier. If something were to happen and the Internet were to go out for an extended period of time, tens-upon-tens of thousands of businesses, including ours, would likely cease to be. The truth is that we’d pay what we’d have to pay for Internet service.
For individuals who have come to depend on the Internet, they likely feel the same way. There is a story of Stamford professor, Jeff Hancock, who used to ask his students to try and stay off the Internet for 48 hours over the weekend and see how it affected their lives. In 2009, when he assigned the task, “...there was a class revolt,” Hancock said, “The students emphatically said the assignment is impossible and unfair.” They stated several reasons for their near-constant Internet use, but it was clear that the biggest reason is that every one of those students had a mobile device that had made near-ubiquitous Internet accessibility a major part of their lives. They paid for access, and didn’t think it was reasonable for their professor to run rough-shot over their lives (for 48 hours). This new world that is so dependent on computing can be seen in the numbers. In September of 2009, a quarter of the world’s population, 1.7 billion people used the Internet. That number would double by December of 2013.
This growth in demand for Internet access (affordable or otherwise), which you can now see in parts of central Asia and Africa, created markets, which in turn created more markets, and nearly overnight, the Internet went from what could be considered a novelty to a must-have utility-like entity--as necessary as food and water to some. In fact, it’s easy to relate. Think about how much you use the Internet. It’s enough to purchase it for your home AND for a mobile device. If you take your mobile data plan into account, the average U.S. and U.K. consumer pays over $100 a month (just over £73) to have near-ubiquitous Internet service.
The invention of social media has made it even more necessary to people. In the United States alone, over half of people (nearly 180 million) use social media. As a culture, we rely so heavily on it, the President uses social media nearly every day to comment on situations, and in some cases, state changes to federal policy. The combination of mobile devices and social media, e-commerce, and secure payment has created an insatiable demand for Internet access, Internet-based services, and the speed to properly broadcast all the content that people today have come to use.
In some places Internet costs more, and people pay it. In fact, people have so bought into the Internet that a whole generation of people would be completely lost without access to it. Whether that is a problem or not is a matter of opinion, but whether you pay $60 a year for Internet like the average Iranian, or $3000 per year like some do in Southeast Asia, people will compromise their own well-being for an Internet connection.
The Economy of the Internet
Projecting the economy of the Internet into the future is like projecting anything’s future state. It is largely unreliable. Today, the Internet is going through another shift. Looking past the hosted utility computing craze that we see today, you see a world that is completely connected. The Internet of Things, the title given to the act of connecting all things, is in its infancy, but some estimates have it being as big as 11 percent of the global economy by 2025. This strategy not only warrants the production of products that have the capabilities of being connected, it also makes certain that more money will be put into securing these systems.
The current state of the Internet’s economic success is a hotly debated issue by economists. On one hand, many, like Northwestern professor, Robert Gordon, suggest that as good as the Internet has been at growing economic productivity, it’s shockingly less important than the establishment of electricity-producers at the turn of the 20th century. This is largely because productivity (that is, the creation of tangible goods) has shifted from manufacturing goods to fulfilling service requests. The Internet of Things, however, alters this thought, clearly presenting ways to boost efficiency and revolutionize traditional business operations in manufacturing, transportation, communications, and retail.
The new economy of the Internet is tied up in “things,” but that’s not to say that there isn’t an immense amount of commerce taking place. Ecommerce generates over $2.3 million every minute, every day, or roughly $3.3 billion a day; almost a quarter of which changes hands over wireless mobile networks. These levels of enterprise will be growing exponentially as the IoT grows.
Net Neutrality and Its Elimination
There are currently around 2,700 Internet Service Providers (ISPs) in the United States. With this amount, it is really impossible to consider that there isn’t enough competition. Some critics, however, have stated that there are a handful of ISPs that control access to the Internet for most Americans. The FCC had stated many times that Net Neutrality actually hurt ISP competition. While there were some that would corroborate that claim, many smaller ISP owners considered it only a pain when they couldn’t secure capital that would allow them to deliver service that customers have come to expect. Some even considered net neutrality a good thing, since the money content providers such as Netflix would be forced to invest, would be invested in larger ISPs such as AT&T, Comcast, and Spectrum.
When the FCC decided to roll back the net neutrality laws in December of 2017, it became evident that a more laissez-faire attitude over the regulation of ISPs will have a long-term effect on consumers. Thus far there hasn’t been much of a change, but going forward it will be corporate entities regulating themselves, as the FCC gave up all regulation of Internet providers.
Expect the ISPs to consolidate further through acquisition, and to establish a pricing structure that will allow them to maximize the profitability of their service. It remains to be seen if net neutrality is finished forever, or if the repeal of the mandate will increase infrastructure spending as many of the ISP lobby have suggested.
The Internet is important for individuals and business, alike, and it’s growing larger and larger by the day. The more the third-world develops infrastructure and allows the other half of the human race access to the Internet, the more important the Internet will seemingly become. For more great information about today’s most important technology topics, sign up for our newsletter today.













