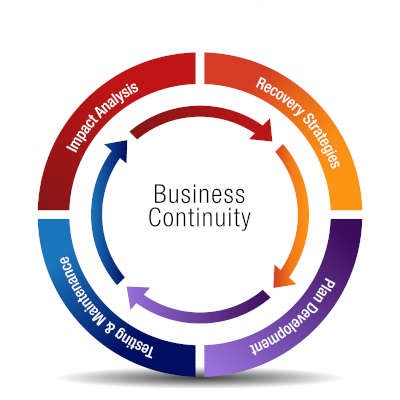
Any business can face a variety of disruptions, from natural disasters to cyberattacks. While many organizations understand the importance of preparing for the unexpected, not all of them have a solid plan in place. A well-crafted business continuity plan (BCP) is crucial for protecting your employees, customers, and bottom line.
Here are some key dos and don'ts to consider when creating your business continuity strategy.