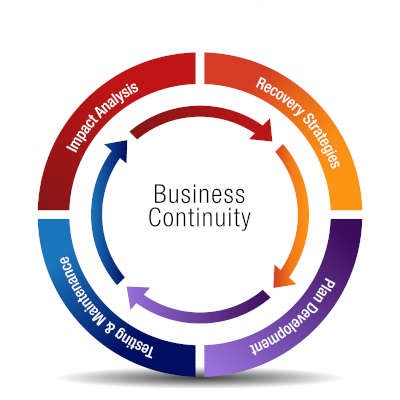
World Backup Day, observed on March 31st annually, serves as a designated occasion to underscore the critical importance of regular data backups for ensuring data continuity. Although this day effectively highlights a fundamental best practice, we firmly advocate for a continuous commitment to maintaining and safeguarding backups rather than confining such awareness to a single day.
Our solutions are built on technology from these trusted industry leaders.