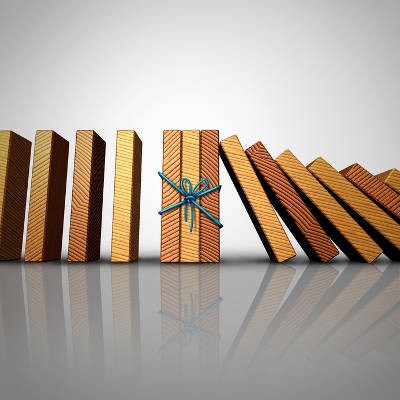
Every business has some sort of management tasks that requires foresight, and staying up on them can keep headache-inducing situations from constantly causing downtime and costing you time; and, make no mistake, time is money. Being more proactive not only provides sound strategies, it can really mitigate the amount of problems you have to deal with. As we describe what it means to be proactive, and how that strategy will almost always help you save money, consider how you are implementing a proactive approach to your business.
Our solutions are built on technology from these trusted industry leaders.