Downtime is a major problem for businesses, and it’s largely a result of technology taking over the workplace. Since many jobs rely on technology to be done properly, it stands to reason that broken-down technology can pose a considerable issue for businesses--not to mention the costs that are associated with downtime and maintenance. A help desk can alleviate some of the pressure that the average employee feels as a result of relying on technology in the workplace.
Telesys Voice and Data Blog
Modern businesses have a lot more room for flexibility than in the past, particularly in regard to meetings. With the inception of conferencing solutions, organizations have access to more dynamic tools to make the most of their meetings. Determining the best one for you, though, is not easy. We’ll help you make that choice in the simplest terms possible.
How well do your employees collaborate with one another? Teamwork is essential to the success of any business, but it’s often something that doesn’t come naturally to some users. These days, there are ways you can make communication and teamwork more effective and efficient for your workforce. This week’s tip is dedicated to making this work.
You can’t have a successful business without a little bit of productivity. Unfortunately, some office environments can have a negative influence on the way your employees get their work done. Take a moment to ask yourself this question: “Are you simply busy, or are you actually being productive?”
These days most consumers lean heavily on their payment cards. Whether they use credit cards, debit cards, or gift cards, consumers today are much more apt to use their card then they are to use cash. Why is this? Convenience mostly, but also there is a belief that using a payment card is more secure than walking around with a wad of cash in your pocket. Today, we will get to the bottom of the matter.
Even if we’d like it to last forever, business technology can’t possibly do so for a number of reasons. Due to the fact that businesses and their technology are constantly upgrading and changing, it’s almost a certainty that you’ll have to upgrade your technology at some point, whether it reaches its end-of-life event or just simply becomes obsolete for your organization. In fact, failing to update your infrastructure from time to time can have serious negative side-effects for your business.
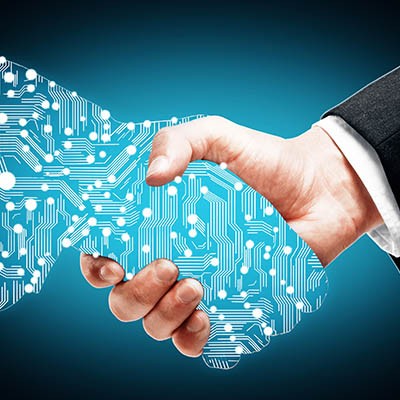
Information technology plays a crucial role for today’s businesses, but in order for it to do so, these businesses need technology to use. IT procurement is a crucial part of any business’ success, which means that any business needs to have a provider that can deliver the value that they need.
If you use Facebook, you’re not alone. There are over two billion active users on the platform. Whether you are willing to accept it or not, Facebook is a huge part of a good chunk of the world’s lives. If being a well-connected, with the times, user has always described who you are, then we could have some helpful information oriented towards you in our blog today. We will be discussing your online identity, and who you have told Facebook you are.
Technology plays an integral part in just about all modern businesses in some way, shape or form. Without a place to purchase devices, however, no one can reap the benefits of them. Some businesses are vendors that provide organizations with these devices. In a sense, they act as the middle man between the producer and the consumer, acquiring devices for sale to businesses and users alike. In this way, vendors are critical for every single business.
Revenue is a key component of any business, crucial to the continued success and efficacy of it. However, in order to sustain an incoming revenue stream, a business needs to be able to operate efficiently enough to support it. In this week’s tip, we’ll review a few ways that you can build this efficiency in your own operations to assist your efforts to build a prosperous business.
The Internet is rife with potential threats. Some are situational, but most are deliberate actions made by malicious entities who are trying to obtain any semblance of value from you or your company. Some of these exploits have been around longer than you’d imagine possible. This has been made evident by huge Internet-based companies such as PayPal and Facebook testing positive for a 19-year-old vulnerability that once allowed hackers to decrypt encrypted data.
Businesses should value organization, collaboration, and usability. There are few tools greater than what Microsoft has offered for nearly the last 30 years to fulfill these values. Excel, Word, PowerPoint, and so many more great tools are available to your business. Today we thought we would go over what other useful tools are available through Microsoft, and how your business can utilize each of them.
Let me ask you a question… let’s say that you’re about one year from your projected retirement, when a ransomware attack encrypts all of your files. What do you do? Pack it in and retire early? This is precisely the situation that the practitioners of Brookside ENT & Hearing Services of Battle Creek, Michigan, have found themselves in - and it may not be over yet.
In parts one through four we talked about choosing the right specifications for your desktop, depending on its role. We talked about selecting the right CPU, RAM, storage, and display options. This final post we hit a few other tips and ideas we came up with that didn’t fit into the other posts.
If you take a look at any computer in an office environment, there is a solid chance that it is running the Windows operating system. Whenever we have the opportunity, we like to share tips and tricks to help both normal and power users alike get the most out of their operating system. Follow these tips and you’ll be able to make navigating your computer just a little bit easier.
The modern office is filled with distractions, and that’s to say nothing about the everyday user’s life. With so many devices and notifications interrupting focus for users all over the world, it’s more important than ever before to have a strategy for how to deal with these issues and become as productive as possible in the workplace. Today, we’ll be discussing some of the biggest distractions in the workplace and how your employees can overcome them.
‘Twas the night before Christmas, and with all the work done,
The office was closing for some holiday fun;
Their coats buttoned up, they had all saved their files,
Everyone’s face creased in a big, toothy smile.
For most businesses, technology has a major role in what they do. They use it in all manners of ways, but there is no question that it has become a driving force for business. As the calendar flips to a new decade, we thought that it would be good to take a look at what the 2010s brought us, and what to expect in the 2020s.
You’re likely aware that we have a Help Desk for our clients to leverage, but not all companies handle their support the same way. Here, we wanted to share a few reasons that we are confident that our approach to support is better for our clients.
Today is the first day of the third decade of the 21st century. For some, it’s just another year, but for others it seems almost impossible that we’ve reached this point without floating cars and manned missions to Jupiter. Fifty years ago, some of the technology that is used in the course of doing business was simply fiction or conjecture. We thought it would be neat to take a look at some of the technological changes made since 1970.
Mobile? Grab this Article!
Tag Cloud