The funny thing about ransomware is that they give them very strange names: Bad Rabbit sounds like the name of a villainous bunny who gets his comeuppance in some type of modern nursery rhyme, not malware that would ravage hundreds of European businesses. Locky seems like the son of Candado de seguridad, a character Medeco would come up with to educate kids on proper physical security. The latest in a long line of funny-named ransomware, SamSam, isn’t a pet name for your pet ferret you perplexingly named Sam, it is one of the worst ransomware strains ever, and it has caught the attention of U.S. Federal law enforcement.
Telesys Voice and Data Blog
Microsoft is coming to the end of its support for the wildly popular Windows 7 operating system, but that doesn’t mean that they won’t make a contingency plan for those organizations that haven’t yet made the jump to new systems. It just won’t be cheap. We’ll break down the upcoming Windows 7 end of life event, and how Microsoft is offering an olive branch of sorts to organizations that simply haven’t upgraded away from this OS.
Businesses are driven by processes. More often than not, these processes are fairly definitive - do this, then do that, then do the other thing - and require a set order of operations. There also happen to be a lot of these processes, which makes it important that they are well-documented so you and your employees can refer to this documentation later. Here, we’ll offer a few tips on how to best document a task.
Small and medium-sized businesses (SMB) have historically been restricted in what they can do with their technology infrastructures. However, there are now options that an SMB can leverage that enable it to accomplish more with their infrastructure - but this requires the SMB to have a plan in place.
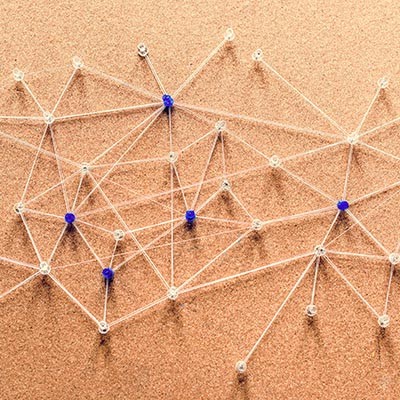
Manufacturing products is still a major part of the western economies; and, like other businesses, manufacturers are using information technology to fuel and manage their supply chains and business processes. We’ll take a short look at what IT manufacturers use, and how it helps them forge their business ahead.
Emails are a wonderfully useful solution, and quite possibly one of the most commonly used ones in the workplace today. However, not everyone is using every capability that their email solutions offer - and it has led to a lot of time being wasted in the workplace. For this week’s tip, we’ll review how to help cut back on the time spent organizing your emails.
The IT guy, Jacob left last month: to begin with. There is no doubt whatever about that. He left without an exit interview, and he didn’t seem very pleased with the way the situation played out. You could never tell if Scrooge cared or not. His demands have never wavered. He expected perfection and when mistakes were made, they were approached as catastrophic affronts to the sustainability of the business, even if that wasn’t the reality.
Automation has been a hot button term for some time. Whether it is in reference to robots that manufacturers use to make their assembly lines more effective, the integrated workflows that today’s customer relationship management software presents, or A.I. crawling through mounds of data to help an entrepreneur better understand his/her business, automation is helping businesses move faster and be more agile. Today, we will look at how organizations are using automation, and how, even if it isn’t a big part of your business strategy today, it will need to be in the future.
All Windows machines are capable of leveraging built-in shortcuts. While it might sound ludicrous, using keyboard shortcuts can eliminate the eight days that the average employee spends every year moving between the keyboard and mouse. Shocking, right? Keyboard shortcuts let you retake all of that lost time and use it to be more productive.
When we discuss our service offerings, we understand that it can all seem like a little much, especially to the small business that - up to this point - has never needed all these fancy solutions to operate effectively. However, there are a few considerations that the business this scenario applies to needs to account for. For instance, is it certain that these solutions are unnecessary?
Data security isn’t the easiest thing in the world to plan for, especially if your organization doesn’t have any dedicated security professionals on-hand. While protecting your data with traditional methods, like passwords, firewalls, and antivirus, is important, what measures are you taking to make sure a thief or hacker isn’t just walking into your office and making off with your technology?
Microsoft PowerPoint is a well-known solution - well-known enough that the product has become synonymous with the task, regardless of what program one happens to use. Of course, this doesn’t mean that one necessarily must use it to create a presentation to go with a sales pitch. For this week’s tip, we’ll suggest a few other tasks you could complete with the help of a PowerPoint presentation.
Improvements in technology have allowed us to come a long way since the days of our ancestors, which is made exceptionally clear by our developments in the realm of healthcare. There are so many ways that healthcare providers can use information technology to their advantage, so we’ll cover a select few here.
Chances are you have a Google account, whether it’s for business or personal use. It’s more accessible today than ever before and provides a solid way to gain access to several important features and accounts. Considering how much can be done with a Google account, users forget that they can put their security and personal data at risk. Here are some ways that your Google account is at risk, as well as what you can do to fix it.
Are you a person that has traditionally written down things in notebooks? If you are, you probably have dozens of notebooks that are half filled with information, most of which you’ll look at sometime in the future and you’ll be reminded just how helpful that note would have been if you had it when you needed it. Today, digital notebooks offer the same helpfulness, with a few added features that make them (dare we say it) a little better than the traditional notepad.
With the smartphone market losing ground for the first time in its short history, many of the manufacturers you’ve come to know are either non-factors in the current market, or don’t even produce smartphones anymore. With new demand growing every year, new manufacturers such as OnePlus and Xiaomi are primed to fall in line behind Samsung and Apple.
Quick question for you: how many email accounts do you have? How many do you have to regularly check? How many different platforms do they utilize? If there’s too many, important communications are easy to miss in the ensuing mess of messages. Fortunately, there are a few ways that this can be avoided, which we’ll review for this week’s tip.
Late in the summer this past year there were several articles written about how Google would continue to track the location of a person’s smartphone after they had chosen to turn their location settings off. A Princeton researcher corroborated those claims for the Associated Press, traveling through New York and New Jersey with locations services off only to be tracked the entire way. Today, we will discuss this issue, and tell you what you need to know to keep Google from tracking you wherever you go.
The modern cyberattack is more of a slight of hand than it is a direct attack. With encryption protecting a lot of business data, hackers need to find ways to circumvent that technology. They often do this though phishing. This week, we will take a look at some of the warning signs of phishing to help give you a little better awareness.
Smartphones are a marvel of modern ingenuity. After looking at employee smartphone use as a problem for much of the past few years, today’s businesses have begun to amend that strategy and are now using employee devices to their advantage. With such a large percentage of today’s workers actively using smartphones, it only makes sense for businesses to try and incorporate their employees’ devices into their day-to-day operational strategy. Today, we’ll take a look at smartphones and how they’ve managed to go from nuisance to necessity.
Mobile? Grab this Article!
Tag Cloud